[ad_1]
Ransomware assaults have an effect on every thing, together with healthcare services, pharmaceutical firms, tech companies, and motels and casinos in Las Vegas. Ransomware has reached a report excessive, with funds exceeding $1 billion in 2023. Why is that this malware so infamous? The identify “ransom” instantly offers it away. You is perhaps involved about this malware in your Android or laptop. This is all about ransomware and the way to shield your self so nobody can extort you utilizing your high-end Chromebook.

Can Chromebooks get viruses?
This is what it is advisable to find out about viruses, malware, and your Chromebook.
What’s ransomware?
Ransomware is malicious software program (malware) that infiltrates computer systems and restricts entry, holding the system hostage till a ransom is paid. This sort of malware has been round for a number of years. The AIDS Trojan has a storied previous that stretches again to 1989, lengthy earlier than the widespread use of the web for disseminating malware.
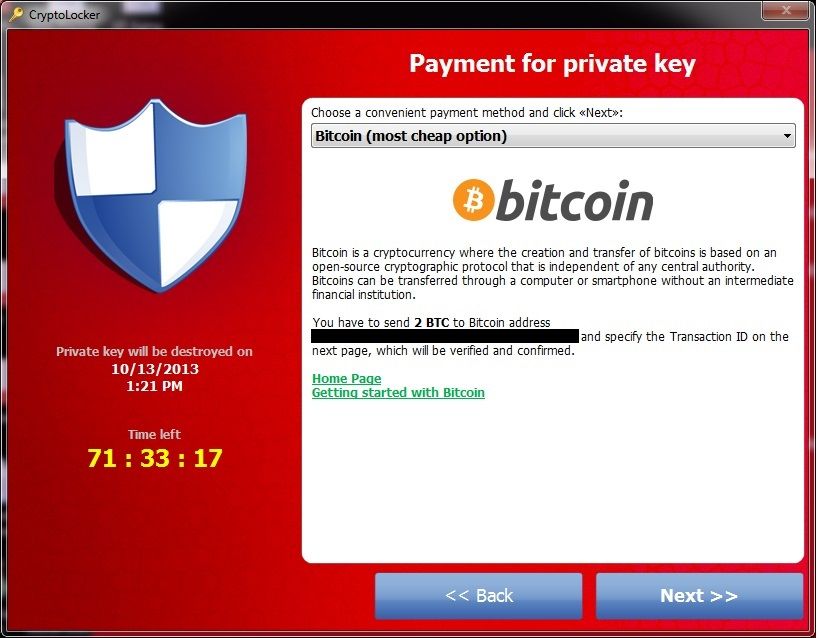
Ransomware tries to power victims to pay by displaying an on-screen message. These alerts typically point out that the system has been locked or information encrypted, warning that entry will stay blocked with no ransom fee. The quantity requested can differ and is often demanded in a digital forex like Bitcoin to acquire a decryption key.
Sorts of ransomware
Ransomware has developed through the years, with totally different traits and assault strategies.
Encryptors
That is the commonest type of ransomware. It encrypts the sufferer’s knowledge and information utilizing sturdy encryption methods. Attackers then demand a ransom in alternate for the decryption key. Noteworthy examples of this sort embody WannaCry and CryptoLocker.
Supply: Avast
Lockers
Locker Ransomware takes a special strategy than encryptors. It would not encrypt information. As a substitute, it locks the sufferer out of their machine. Victims discover themselves locked out from their information, functions, and system settings, with a ransom message showing on the display.
Scareware
This ransomware acts like bogus antivirus or cleansing instruments. It bombards customers with pop-ups and phony menace notifications, insisting that paying a charge will clear up any points. Though it is not as damaging as encryptors or lockers, it may be irritating and generally consists of threats to delete information.
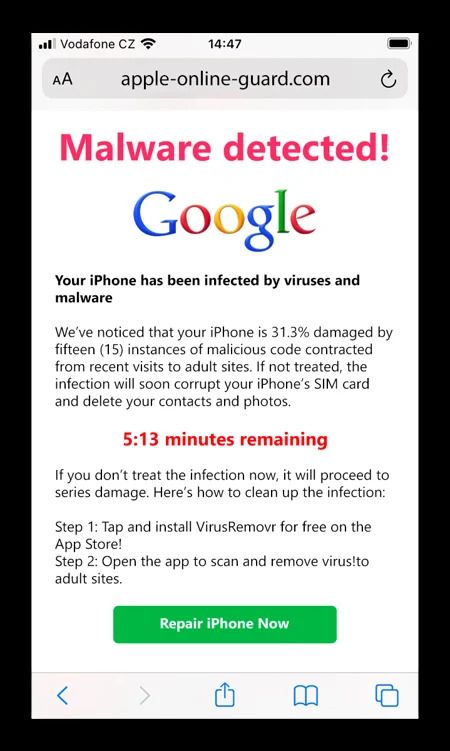
Doxware or Leakware
In Leakware situations, moderately than erasing knowledge, the attacker threatens to make it publicly out there. Additionally known as Doxware, these assaults primarily goal organizations reminiscent of banks and authorities businesses, which handle prone data.
RaaS (Ransomware as a Service)
On this mannequin, ransomware creators monetize their software program by promoting or leasing it on the darkish internet, permitting different associates to hold out assaults. The ensuing earnings are divided between the malware creators and the attackers.
Double extortion
It is a extra aggressive tactic the place attackers do greater than encrypt knowledge. Additionally they steal it. They then threaten to publicly launch the stolen knowledge if the ransom is not paid, even when the information are decrypted. This tactic will increase the strain on victims, compelling them to conform.
Triple extortion
Triple extortion ransomware takes the idea of double extortion one step additional by introducing a 3rd layer of coercion. This typically includes demanding a ransom from the sufferer’s enterprise companions or prospects or escalating their assaults with a distributed denial-of-service (DDoS) towards the sufferer’s firm.
Widespread ransomware assault patterns
Familiarity with the frequent methods of those assaults is vital for establishing efficient defenses and decreasing dangers. This is a rundown of widespread assault patterns.
Phishing assaults
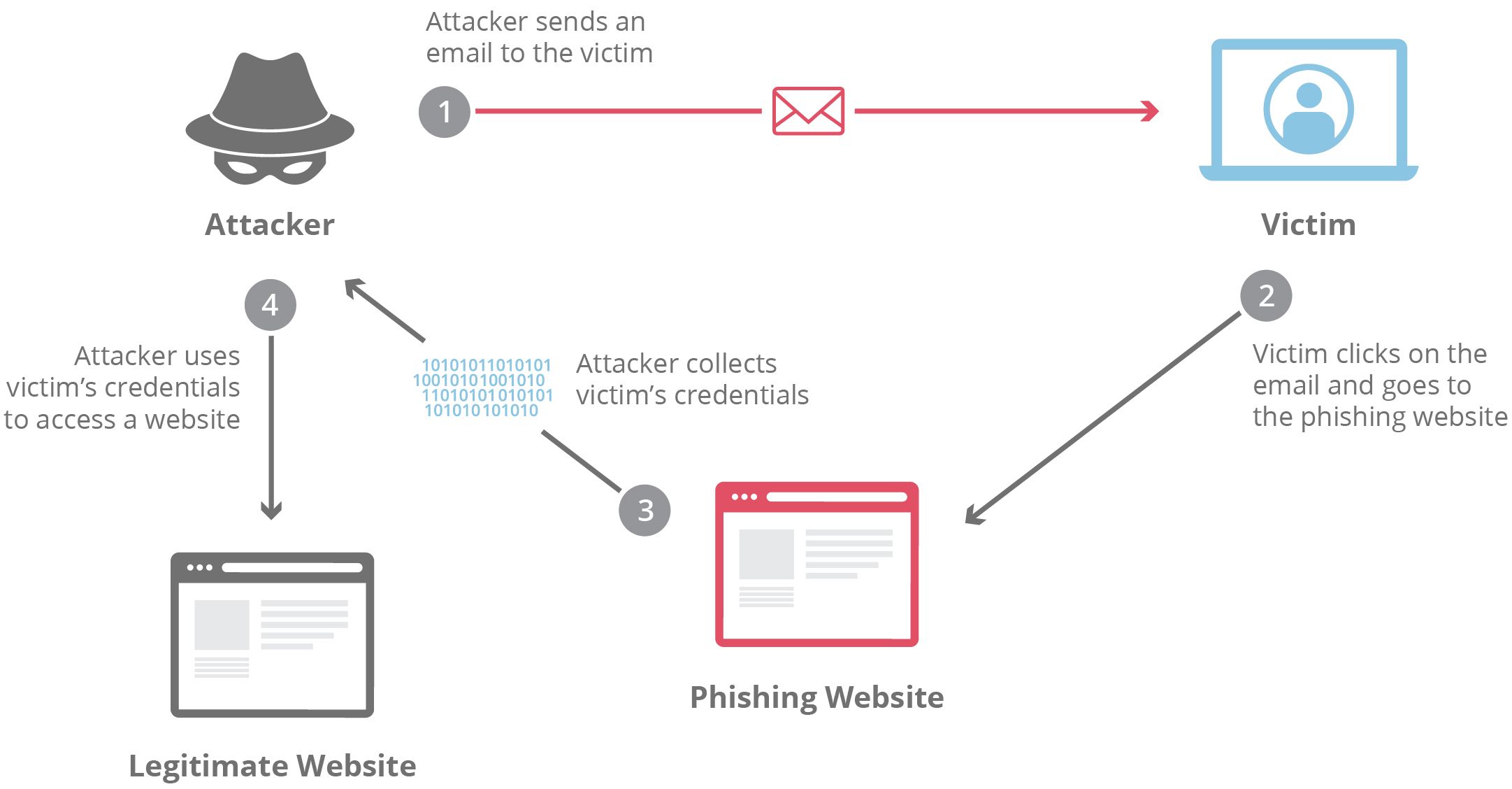
In line with a examine by Deloitte, 91% of cyberattacks begin with phishing and spear phishing messages. Hackers favor these methods to sneak ransomware into techniques. They sometimes put together by researching their targets totally. Afterward, they ship persuasive emails with hazardous attachments like ZIP information, PDFs, and spreadsheets with embedded malware. These emails may comprise hyperlinks to misleading web sites cleverly designed to deceive you into downloading ransomware that threatens to compromise your community.
Supply: Cloudflare
Malicious adverts
Malicious promoting, also referred to as malvertising, is more and more used to distribute ransomware. Hackers buy actual promoting house on this scheme and hyperlink it to an exploit package. If you click on these adverts, the package scans your system for particulars like working system, software program, and browser specifics. It tries to deploy ransomware in your laptop if it finds a vulnerability.
Utilizing pirated software program
Pirated software program and software program bundled with adware are pathways for ransomware entry. Customers who interact with pirated software program improve their danger of ransomware assaults and miss essential safety updates resulting from not receiving official software program patches, making them extra weak to such assaults.
Moveable computer systems and USB drivers
Laptops are sometimes susceptible to ransomware assaults since they sometimes retailer giant quantities of delicate knowledge and are integral to our every day work. Equally, USB drives are a popular instrument for delivering ransomware. Their ease of transportation and skill to hook up with numerous computer systems make them significantly efficient.
When a malware-laden USB drive is inserted into a pc, it robotically executes the malware, infecting the system and probably spreading ransomware to all gadgets on the community.
Public Wi-Fi
Public Wi-Fi is a standard hiding spot for ransomware. If you entry delicate data in public areas (suppose the native Starbucks), think about switching to safe 4G or 5G entry or utilizing a VPN to guard your knowledge when working outdoors the workplace is unavoidable.
Greatest VPNs for a number of gadgets in 2024
It solely takes certainly one of these VPN subscriptions to cowl your complete fleet of computer systems, cellular gadgets, and streamers
Learn how to defend your self from ransomware
Stop ransomware and decrease harm by following these easy steps.
Again up your knowledge
The simplest approach to shield towards the lack of crucial information is by sustaining backups, each within the cloud and on an exterior drive. Shifting your knowledge to a cloud service simplifies and secures the backup course of towards potential threats. If ransomware infects your system, wipe your machine and restore your information from these safe backups.
Make sure the techniques the place you retain your backups cannot change or delete them. Ransomware actively seeks out backups to encrypt or delete them, rendering them unrecoverable.
Use safety software program and replace it usually
Hold all of your computer systems and gadgets safe by putting in sturdy safety software program, and do not lag behind on software program updates. Common and well timed updates are key to defending your techniques towards the most recent threats.
Defend your digital life
Being cautious is your greatest protection. Assume earlier than you faucet or click on. Do not reply to emails and textual content messages from unfamiliar contacts. Plus, prohibit your app downloads to trusted sources and use protected searching. This easy precaution can prevent from pointless safety dangers.
[ad_2]