[ad_1]
Leaking or hacking of birthdates and social safety numbers (SSNs) is harmful as a result of these items of knowledge are crucial to verifying an individual’s identification. With entry to somebody’s birthdate and SSN, malicious actors can commit identification theft. When that occurs, risk actors can apply for credit score, drain your financial institution accounts, or acquire companies within the sufferer’s title, resulting in monetary loss, broken credit score rankings, and extra.


So, the subsequent time you’re in a bar, down a few beers, please don’t say “Hey, I used to be an AT&T shopper again in 2021” and, ten seconds later, “I’ve an entire Bitcoin, bro, how cool is that!?” to a bunch of full strangers.
The truth is, don’t inform anyone something concerning your funds. Bob’s your uncle.
SIM swap, eSIM swap
Let’s not get paranoid, however the extra expertise we incorporate in our lives, the extra choices for evildoers to steal from us. Now, since we like having and utilizing cell networks, Web entry, electrical energy, and all the opposite goodies of contemporary life, we’ll must type issues out and take precautions.
Each good protection technique begins by understanding your enemy’s assault technique. In different phrases, we’ll have to grasp what’s occurring with a purpose to take measures.
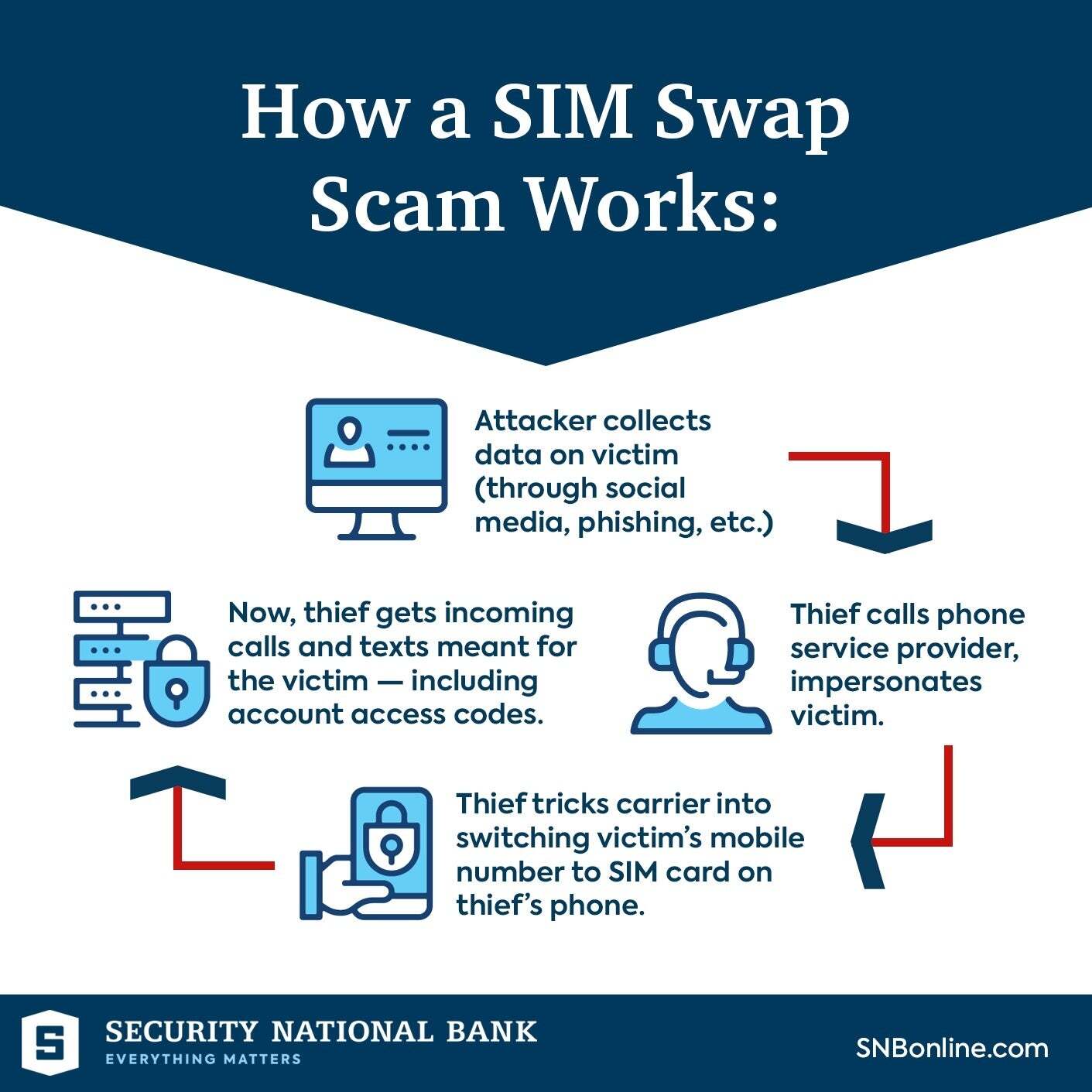
By pretending to be you through identification theft, wrongdoers may have interaction in what’s often called SIM swap.
SIM swap fraud is a kind of identification theft the place criminals deceive a service into transferring a sufferer’s telephone quantity to a SIM card within the fraudster’s possession. By doing so, the attacker features management over the sufferer’s telephone calls, textual content messages and doubtlessly entry to safe companies that depend on phone-based authentication, similar to two-factor authentication (2FA) for banking or social media accounts.
This enables the prison to bypass safety measures and entry private data – in essence, all calls and messages go to the prison who can fake to be the sufferer, after which proceed with the checking account emptying.
On a facet word: I ponder what number of of these impersonations are aided by AI and its magical capabilities. Sigh…

So, what’s an eSIM fraud? In essence, it’s the identical factor as SIM swap, solely simpler.
That’s as a result of the truth that eSIM (or embedded SIM), is a digital model of a standard SIM card that lets you activate a mobile plan with out having to make use of a bodily SIM card. It’s extra handy for unhealthy actors, as they don’t must take a stroll to a service’s workplace. It’s all digital now.
The eSIM is constructed immediately into your system, like a smartphone, smartwatch, or pill. It’s a small chip that is already put in in your system and also you need not insert or substitute it. To activate it, you normally scan a QR code supplied by your cell service. This course of hyperlinks your system to your cell account with out the bodily swapping of SIM playing cards.
Total, eSIM expertise provides comfort, flexibility and effectivity, making it simpler to handle your cell companies immediately out of your system.
“Because the fall of 2023, analysts from F.A.C.C.T.’s Fraud Safety have recorded greater than 100 makes an attempt to entry the private accounts of purchasers in on-line companies at only one monetary group”, says cybersecurity agency F.A.C.C.T.
SIM swap frauds are on the rise in 2024


Sadly, there are many examples solely in 2024 concerning the SIM/eSIM swap fraud phenomenon.
Simply final week, an entire household of 5 acquired their Cricket Wi-fi account taken over and cash was stolen from the household’s monetary apps.
Nonetheless, Mike, his spouse and their household from the Chicago suburbs had been locked out of their Amazon, social media, funding, and cryptocurrency accounts. The hackers managed to make unauthorized adjustments to the telephone’s content material, including apps and altering contact data. Moreover, the household misplaced $1,200 in cryptocurrency, $2,000 in Apple Money and Present Playing cards and narrowly prevented unauthorized financial institution transfers.
In February, a T-Cellular subscriber acquired an electronic mail from his service. In it, it was said {that a} SIM change on his quantity had been accomplished. The issue is that he had by no means requested such an operation… He found that the eSIM on his iPhone was now not energetic.
T-Cellular knowledgeable the person of the state of affairs: an individual had entered a T-Cellular retailer, not removed from the sufferer’s residence, impersonating them to acquire a brand new SIM card. It was used on the prison’s system. Throughout a name with T-Cellular, the sufferer acquired fraud alerts from his financial institution, blocking makes an attempt to purchase luxurious gadgets from malls.
To regain management, the sufferer needed to personally go to a T-Cellular retailer, the place an worker changed the SIM with out alerting the thief through textual content.
Typically, such SIM swap frauds are enacted by service staff. For instance, a former supervisor at a telecommunications firm in New Jersey pleaded responsible to conspiracy fees for accepting cash to carry out unauthorized SIM swaps that enabled an confederate to hack buyer accounts. For carrying the unauthorized quantity porting, the prison acquired $1,000 in Bitcoin per SIM swap, plus an unspecified proportion of the income earned from the illicit entry to the victims’ gadgets.
Now’s the time to vent and announce my full and utter help for harsh penalties for such acts.
In January, Sharon Hussey misplaced $17,000 regardless of utilizing two-factor authentication (2FA) as a result of a SIM swap rip-off. She was alerted to a fraudulent telephone buy and adjustments to her checking account’s contact data, neither of which she initiated. Her incapability to obtain 2FA codes, after a thief swapped her SIM card to a brand new telephone, led to her telephone service being reduce and the theft of $17,000 from her Financial institution of America account.
The rip-off concerned the thief convincing a Verizon retailer to activate a brand new telephone with Hussey’s quantity, gaining management over her 2FA-protected accounts. The state of affairs was exacerbated as a result of Hussey’s reliance on 2FA inadvertently gave the thief simpler entry to her accounts. After initially refusing, Financial institution of America finally refunded the stolen $17,000, highlighting the hazards of SIM swaps, particularly for customers depending on 2FA for safety.
2FA (Two-Issue Authentication) limitations
Two-Issue Authentication (2FA) provides a major enhance in safety by requiring a second type of identification, making unauthorized account entry far more tough even when a password is compromised.
Nonetheless, 2FA shouldn’t be with out its drawbacks. Some customers discover the additional login step inconvenient and reliance on gadgets for authentication may be problematic if the system is misplaced or unavailable. SMS-based 2FA is inclined to SIM swapping and interception, which may undermine its safety advantages. The technical implementation of 2FA poses challenges for organizations, necessitating additional infrastructure and person schooling.
Two-Issue Authentication (2FA) Professionals:
- Enhanced safety: By requiring a second type of identification, 2FA makes it considerably more durable for unauthorized customers to entry your accounts, even when they know your password.
- Diminished fraud threat: 2FA can drastically scale back the chance of identification theft and fraud since attackers want extra than simply stolen login credentials to achieve entry.
- Versatile choices: 2FA provides numerous strategies for the second issue, together with textual content messages, authenticator apps and {hardware} tokens, permitting customers to decide on what fits them finest.
Two-Issue Authentication (2FA) Cons:
- Vulnerability: SMS-based 2FA may be weak to SIM swapping assaults or interception, doubtlessly permitting attackers to bypass this safety measure.
- Inconvenience: Some customers discover 2FA strategies, particularly SMS or app notifications, inconvenient or time-consuming, because it provides an additional step to the login course of.
- Dependence on gadgets: 2FA strategies that use telephones or tokens may be problematic if the system is misplaced, broken, or not instantly accessible.
What the FCC says
In response to the rising risk of SIM swapping and port-out fraud, the Federal Communications Fee (FCC) has rolled out new measures beginning July to reinforce client safety. These adjustments require cell service suppliers to confirm identification completely earlier than a telephone quantity may be moved to a brand new system or service. Moreover, the principles will make it attainable for customers to be instantly notified of any makes an attempt to vary their SIM card or port their quantity.
How you can shield your self from SIM swap rip-off


Defending your self from SIM swap fraud is a fancy matter. It’s a type of artwork, in the event you like. It includes a mixture of vigilance, consciousness and taking proactive safety measures:
- Management your social media posting: Don’t put up each facet of your life on-line. Simply don’t. Be cautious about sharing private data on social media. Scammers typically collect private particulars to convincingly impersonate victims.
- Use robust, distinctive passwords: You’ve heard this earlier than, however… For all accounts, particularly your electronic mail and cell service account, use robust, distinctive passwords and alter them frequently.
- Allow Multi-Issue Authentication (MFA): Use MFA choices that don’t depend on SMS, similar to authenticator apps or {hardware} tokens, for an added layer of safety.
- Safe your cell account: Contact your cell service to arrange further safety measures, similar to a singular PIN or password that have to be supplied to make adjustments to your account.
- Keep watch over your accounts: That is usually uncared for. Repeatedly verify your financial institution and different delicate accounts for unauthorized exercise. Early detection of fraud can restrict injury. Having stated that, be cautious of the place you verify your accounts. You by no means know who’s trying.
- Don’t fall for phishing scams: Be cautious of unsolicited calls, emails, or messages making an attempt to extract private data or urging you to carry out security-related actions.
- Contact service instantly: In case your telephone all of a sudden loses service, or you may’t make calls (or ship texts), contact your service instantly to verify for potential SIM swap fraud.
- Double verify: You could recieve texts from somebody that is pretending to be your service’s consultant. That is why it is essential to double verify each incoming communication by means of one other line of communication. If a service is messaging you about adjustments, do not do something and name them (do not textual content!) to verify if that’s true. In case your telephone is hijacked, incoming coms is perhaps from the malicious actors.
There isn’t a such factor as a 100% safe system (or telephone). However, hey, let’s not make it straightforward for the scammers on the market! Let’s take precautions.
[ad_2]






